Understanding ransomware: effective strategies for organizational protection
Ransomware is a term no longer reserved for IT specialists. In the news, there are numerous examples of ransomware attacks: from (online) stores to media companies, car manufacturers, IT suppliers and even entire governments (most recently the government of Costa Rica in April 2022).
But what actually is a ransomware attack and how does it come about? And more importantly, what can you do as an organization to arm yourself as well as possible against it? And what if an attack has been successful, how do you deal with it? And finally, how do you test whether you as an organization are sufficiently armed?
What is a ransomware attack and how does it come about?
We start with a little bit of history. It is unknown to many that the first ransomware attack occurred in the year 1989 [1]: the so-called AIDS Trojan (also called the PC Cyborg virus). In 1989, the Internet for consumers and businesses was largely nonexistent. Private photos and/or entire administrations of organizations were not yet in the cloud. So how could a ransomware attack occur anyway? Dr. Joseph Popp, an evolutionary biologist created 20,000 floppy disks that he handed out to participants at the World Health Organization (WHO) AIDS conference. When these floppy disks were read by a computer, a program became active that counted the number of times the computer had been rebooted. If the computer had been rebooted 90 times, all directories and files were hidden. A fee of $189 was charged to restore the files.
During the 1990s, email and connecting to systems externally was not yet widely used. Only in the late 1990s, with the introduction of broadband Internet, its use became more and more widespread. At the same time, viruses, malware and ransomware were also on the rise as a result [2].
The National Cyber Security Center (NCSC) provides the following definition of ransomware: "A ransomware attack is a digital attack that renders systems or files unusable by encrypting them, holding data hostage. This hostage-taking is accompanied by extortion, where decryption is offered for payment, usually in crypto-currency" [3].
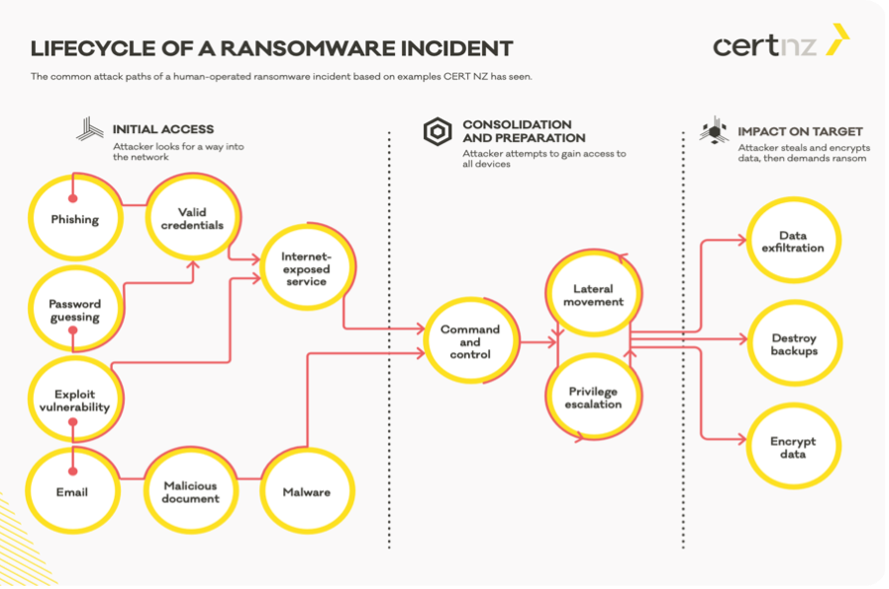
A ransomware attack consists of 3 phases (see Figure 1):
1: Initial access: in this phase, the attacker attempts to gain access to the organization's IT systems. Several methods can be used for this purpose: extracting password data via phishing, guessing passwords (through password hacking tools, for example), exploiting software vulnerabilities and via malware sent by e-mail.
2: Consolidation and preparation: then the attacker tries to gain access to the rest of the network by installing rogue tools and using these tools to gain higher privileges (e.g., administrator access).
3: Impact on the victim: from the third stage, the victim only realizes that an attack is taking place. The attacker now starts downloading data, deleting backups and encrypting the systems (and all associated data).
Now we know how ransomware attacks have historically occurred, what the definition is and how an attacker can enter an organization. The next question then remains: how can I arm my organization against it?
Let me begin by stating up front that a ransomware attack can never be completely eliminated and/or prevented. For this, the attackers have become too sophisticated. In fact, an average hacker is not necessarily also the one who carries out the attack on your organization. Once a hacker has compromised an organization through one of the initial access methods mentioned above, the hacker usually "sells" the organization on the dark web [5] to criminal organizations. These criminal organizations then take over the access and further execute the ransomware attack. Nowadays, there is even a special Ransomware-as-aService (RaaS) revenue model. With this model, criminal developers of malware/ransomware offer their services/software for a fee to other cybercriminals who then use it to carry out an attack.
How can organizations best guard against ransomware?
But as an organization, how do you ensure that you have the least chance of being "ransomed"? A good thing to know here is that attackers always start to attack organizations that are the least secure. Therefore, it is important to get ahead of the "herd" and be more secure than the majority of organizations.
To best arm yourself as an organization, the following 5 key tips are distinguished by NIST [6]:
- Educate employees to prevent ransomware infections
- Do not open files or click on links from unknown sources;
- Avoid using personal websites and apps;
- Do not allow private devices to connect to the corporate network without prior authorization.
- Prevent vulnerabilities in systems that can be exploited by ransomware
- Make sure systems are fully patched;
- Use the zero trust [7] principle for all systems within the network;
- Allow only installation of approved apps;
- Discuss security requirements on ransomware with vendors.
- Detect and stop ransomware attacks and infections as soon as possible:
- Make continuous use of malware detection software such as antivirus software;
- Take advantage of 24/7 network monitoring;
- Block unreliable sources via the Web.
- Make it harder for a ransomware attack to spread:
- Use standard user accounts with multi-factor authentication;
- Use authentication delay or automatic account lockout;
- Manage assigning and periodic review of users and passwords;
- Use "immutable storage" [8] for backups;
- Allow only remote access to the office network via VPN.
- Make it easier to recover stored information in the event of a ransomware attack:
- Create an incident recovery plan;
- Provide secure data backup and test restoring data;
- Keep a record of key contacts who can/should be contacted in case of a ransomware attack.
Another option that many organizations are considering is cyber insurance. This insurance insures your organization against liability for damages caused to third parties by a cyber incident or system intrusion. It also (partially) covers business damage, digital extortion, cyber theft, phone hacking, restoration of software and data and crisis management costs. However, what is not mentioned at first glance on insurers' websites is that a very extensive questionnaire must be completed. Also, very extensive lists of accounts with extensive privileges must be delivered for each system within the organization. If the questionnaire is not completed in the required detail or with the correct answers then the insurance will be rejected.
How do you handle it when an attack has been successful?
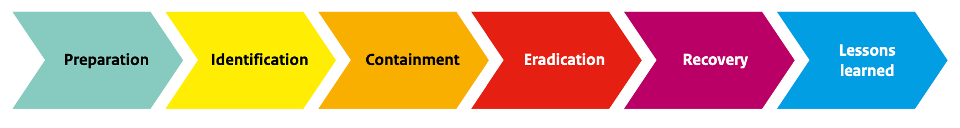
Of course, as an organization you hope it will never happen but, as mentioned earlier, there is always a chance that it will happen despite all measures. To this end, the National Cyber Security Center has created a Ransomware Incident Response Plan [9]. This plan distinguishes between 6 steps (see Figure 2):
- Preparation: this step includes setting up measures to arm yourself as an organization against ransomware (see earlier in this article).
- Identification: next, it is important to timely identify that a ransomware attack has occurred. Here it is important to identify "Patient Zero" so that it can be analyzed how the attacker got in.
- Containment: once it is known that an attack has occurred, it is important to immediately disconnect compromised systems from the network, block accounts and reset passwords.
- Eradication: only when the scope of the entire attack is known can this step be started. Namely, in this step all infected files are deleted and clean images are installed on the affected systems.
- Recovery: when it is certain that all malware/ransomware has been removed from the systems, recovery can be proceeded with. The consideration may be to build a new parallel environment in case of a major attack and transfer systems and data step by step (after thorough auditing).
- Lessons learned: the final step is to put the lessons learned into a report so the organization can learn from the attack for the future.
How do you test whether you are adequately armed as an organization?
Penetration test
A commonly used method to know if you are adequately secured as an organization is to have a penetration (Pen) test performed by a security organization. This involves subjecting your systems and network to a series of technical tests by (ethical) legal hackers with the goal of identifying vulnerabilities. The pen test report then includes recommendations to resolve these vulnerabilities.
Ransomware resilience audit
In addition to this technical method, there is another way to evaluate whether you as an organization are adequately secured: performing (or having performed) a Ransomware Resilience audit.
In a Ransomware Resilience audit, an IT auditor examines whether your organization's internal controls are of sufficient level to prevent, stop and/or recover from a ransomware attack.
Within ARC People, we use the Cyber Security Evaluation Tool [11] (CSET) from the Cybersecurity and Infrastructure Security Agency (CISA) as a standards framework for our clients. The standards in this standards framework are derived from the most common cyber security standards and publications, including: National Institute of Standards and Technology (NIST), Center for Information Security (CIS), National Cybersecurity Center of Excellence (NCCoE) and Cyber Security Evaluation Program (CSEP).
This standards framework distinguishes 48 standards divided into the following 10 categories: Robust Data Backup (DB), Web Browser Management and DNS Filtering (BM), Phishing Prevention and Awareness (PP), Network Perimeter Monitoring (NM)
Asset Management (AM), Patch and Update Management (PM), User and Access Management (UM), Application Integrity and, Allowlist (AI), Incident Response (IR) and Risk Management (RM).
As an outcome, we prepare a report that differentiates between 3 maturity levels for each measure: Basic, Intermediate and Advanced (including practical tips to meet a higher maturity level if desired).
Conclusion
You cannot completely prevent a ransomware attack, but the trick is to be more secure than others. Over the years, fortunately, clear knowledge has accumulated about ransomware attacks: what it is and how it originates. There are also increasingly clear guidelines on how to guard against it as an organization and - once it does happen to you - recover from it. As ARC People, we believe that performing a periodic Ransomware Resilience audit (in addition to the annual pen test) gives you as an organization a good overview of the extent to which you have the proper management measures in place to prevent, stop and/or recover from a ransomware attack. Our experts are happy to help you perform this audit as part of your annual internal audit plan or as a separate audit.
Want to know more? Then contact Anita van der Leeuw for the possibilities!
Anita van der Leeuw is senior manager of IT Audit & Risk at ARC People.
[1] Kelly, Samantha Murphy (May 16, 2021). " The bizarre story of the inventor of ransomware". CNN Business. Warner Bros. Discovery. Archived from the original on May 16, 2021
[3] Ransomware incident response plan, National Cyber Security Center, May 2022.
[5] The dark web is a part of the worldwide web that is not directly findable by search engines (so-called non-indexed websites or deep web). The dark web is part of the deep web but is only accessible with special software that provides the user with anonymity, such as Tor, I2P or Freent (source: www.wikipedia.org).
[6] Barker et al. (2022). Ransomware Risk Management: a Cybersecurity Framework Profile. National Institute of Standards and Technology (NIST). https://nvlpubs.nist.gov/nistpubs/ir/2022/NIST.IR.8374.pdf
[7] Use network segmentation whenever possible and manage access to all network functions.
[8] Immutable storage is a way of storing backups that cannot be changed or modified. This is one of the most important safeguards for the organistion in the event of a ransomware attack.
[9] Ransomware incident response plan, National Cyber Security Center, May 2022.
[10] Ransomware incident response plan (page 4), National Cyber Security Center, May 2022.
